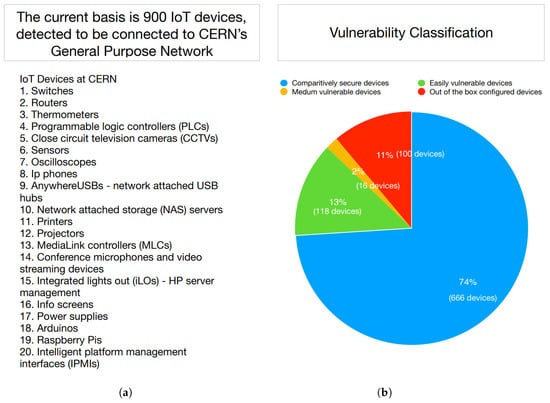
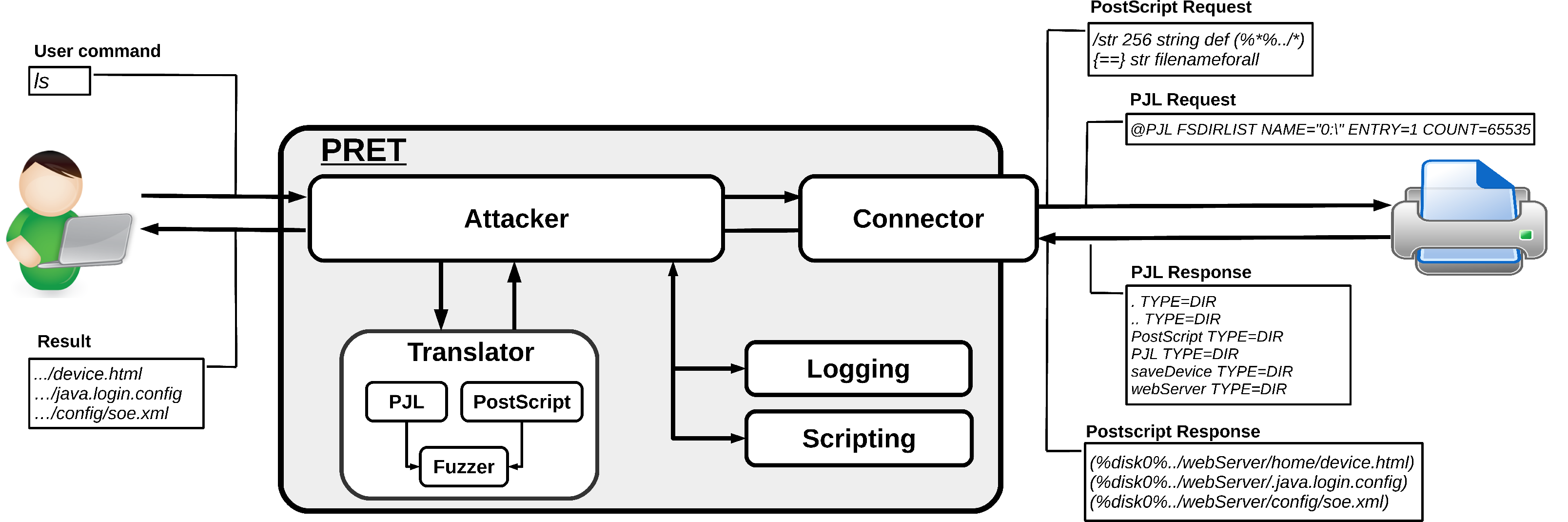
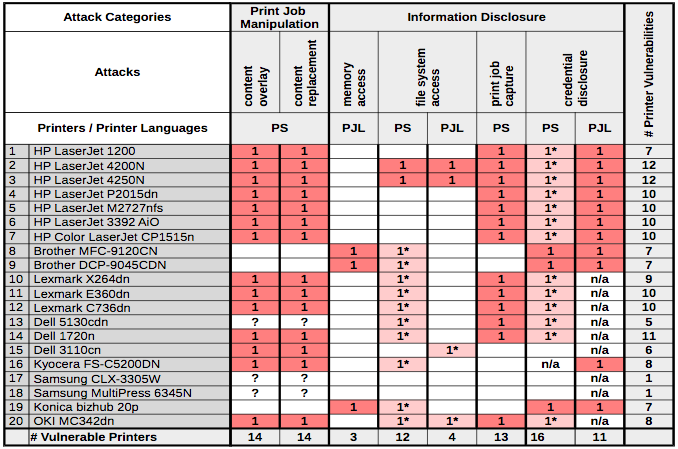
National Cyber Security Services - PRETty:-- "#Printer #Exploitation # Toolkit" #LAN #automation #tool. #PRETty is useful when a large number of printers are present on a #network. Instead of #scanning, logging, and manually

TheHackerGiraffe & PewDiePie Printer Predicament Using The Printer Exploitation Toolkit PRET - YouTube

Strategies to End Commercial Sexual Exploitation of Youth: A toolkit for collaborative action | National Center for Youth Law

Strategies to End Commercial Sexual Exploitation of Youth: A toolkit for collaborative action | National Center for Youth Law