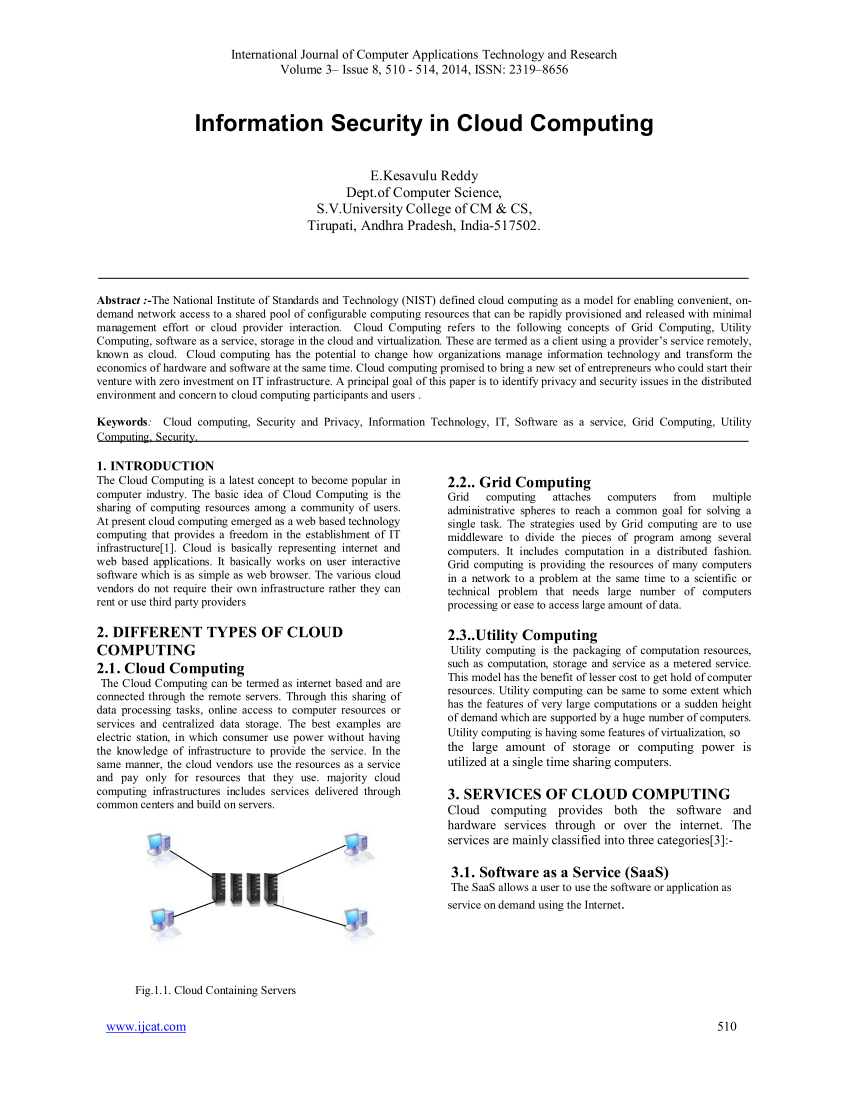
Cloud Computing Security How Does Cloud Security Work Ppt Introduction | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Data Security and Privacy in Cloud Computing – topic of research paper in Computer and information sciences. Download scholarly article PDF and read for free on CyberLeninka open science hub.

Learnuva - BCA - Ethical Hacking, Cyber Security, Cloud Computing, Data Science, Artificial Intelligence In this technological world, information technology and communication systems have become an important part of the strategic planning

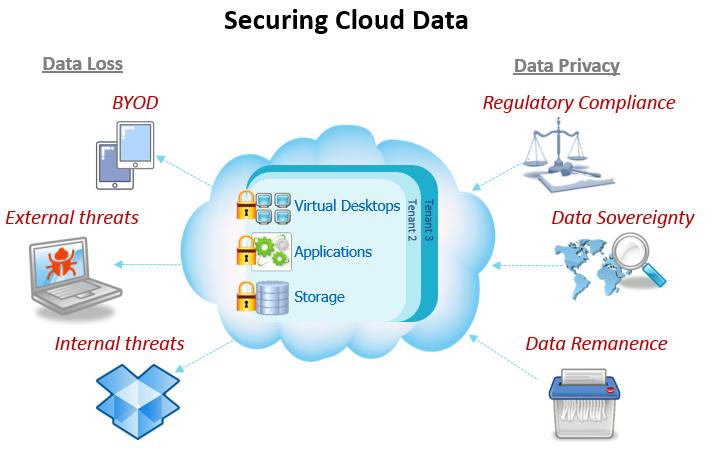
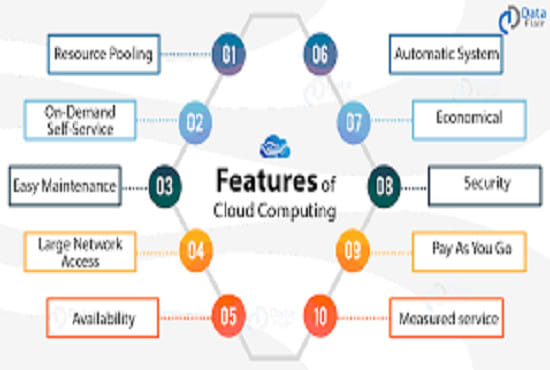





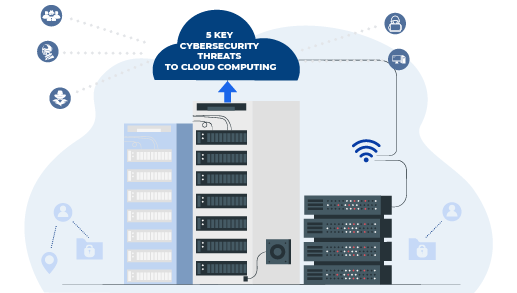




![PDF] Introducing a Security Governance Framework for Cloud Computing | Semantic Scholar PDF] Introducing a Security Governance Framework for Cloud Computing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3037b74aaa48564d9b1d64ae5084db628dc0aaee/5-Figure1-1.png)