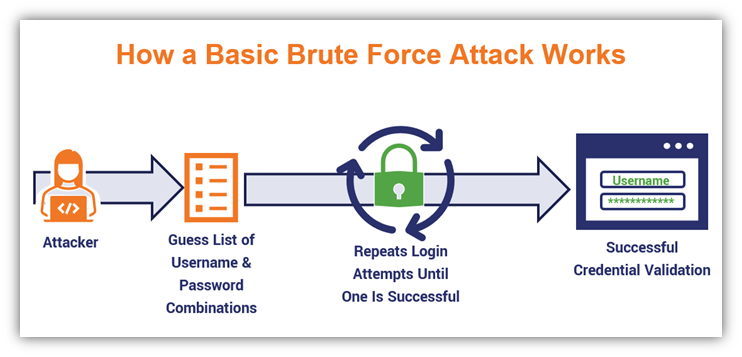
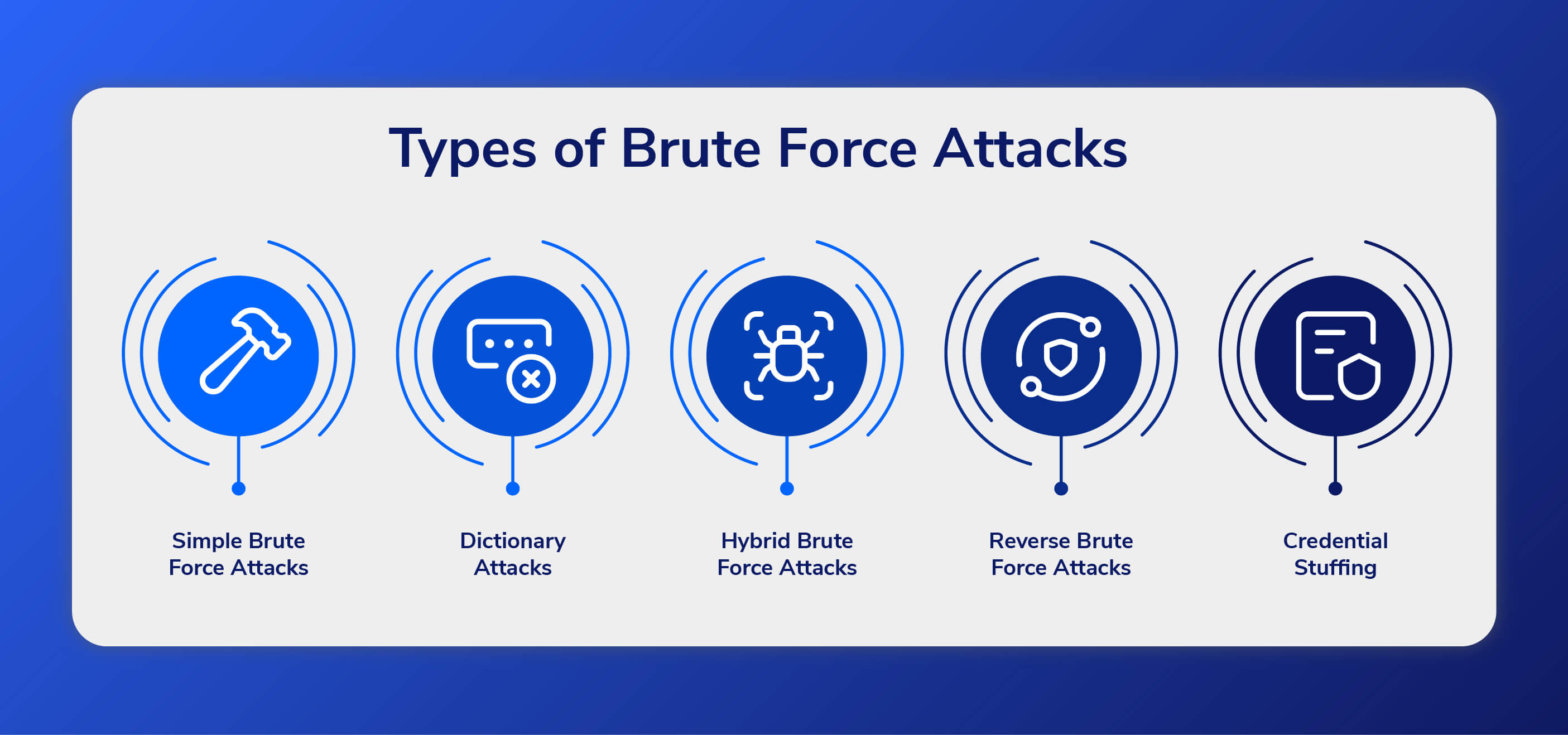
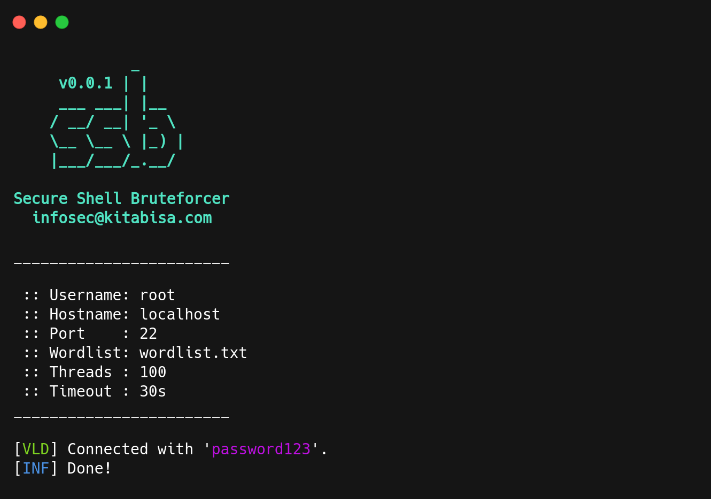
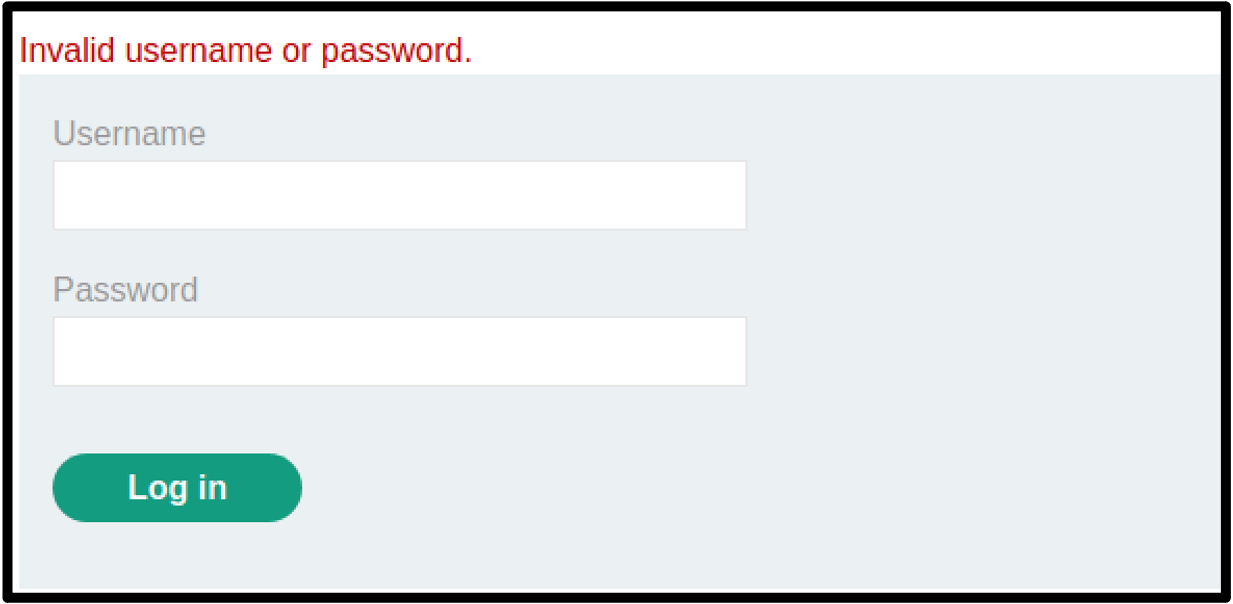
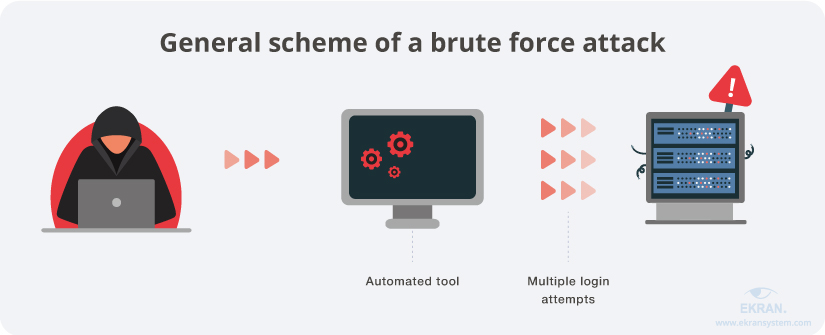
SECURITY] Insufficient Anti-Automation – Brute Force Attack · Issue #991 · directus/v8-archive · GitHub

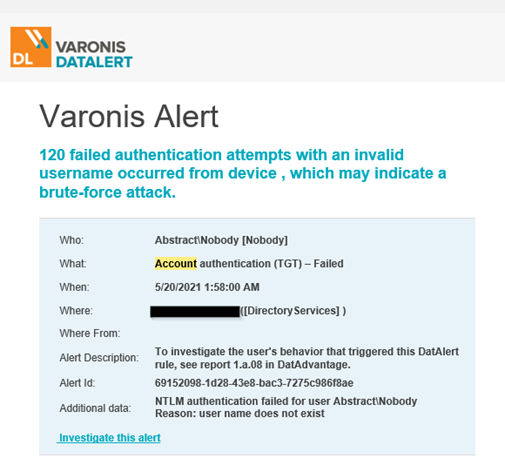
How Does HSS Block Brute-Force Attacks?_Host Security Service (Old)_FAQs_Alarm and Event Management_Brute-force Attack Defense_Huawei Cloud

How Do I Handle a Brute-force Attack Alarm?_Host Security Service (Old)_FAQs_Alarm and Event Management_Brute-force Attack Defense_Huawei Cloud