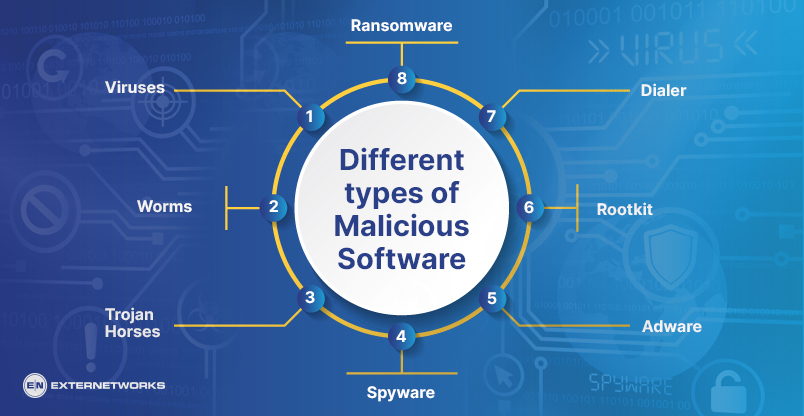
SC MCQ 2109 - Security in computing mcq - Category: I Marks: 1 Which of the following is independent - Studocu

WORKSHOP INSTRUCTOR/INSTRUCTOR GRII/DEMONSTRATOR/DRAFTSMAN GR II INFORMATION TECHNOLOGY TECHNICAL EDUCATIOIN : page 6 - Kerala PSC Question Paper

191588501 Solved MCQ of Computer Security and Network Security - Solved MCQ of Computer Security set - Studocu